NFC is a type of radio communication standard, just like Bluetooth, WiFi and other networking technologies. The difference is that NFC only works when two devices are in close proximity to one another. It also operates at slower speeds. In addition, NFC can read RFID chips and it can be used for mobile payments. To exclude malicious parties and eavesdroppers Microsoft found a method to better secure NFC in the future.
Secure NFC
Microsoft Technology Licensing filed a patent with WIPO on January 27, 2017. The patent was published on January 30, 2018 and is titled: Secure near field communications. The patent describes the following situation and solution:
NFC has historically relied on proximity as a security feature, but as malicious parties and eavesdroppers gain greater sophistication in their receiving hardware and in disguising devices to implement man-in-the-middle attacks at the point of data exchange, additional security features are needed to maintain confidence in the privacy of NFC transactions.
One of the benefits of NFC is that its handshake process between two communicating devices is fast, so that two devices may exchange data quickly. Unfortunately, part of that speed is realized by foregoing an authentication (e.g., a username/password pair) of the communicating devices and instead relying on the short range of the communications to exclude malicious parties or eavesdroppers.
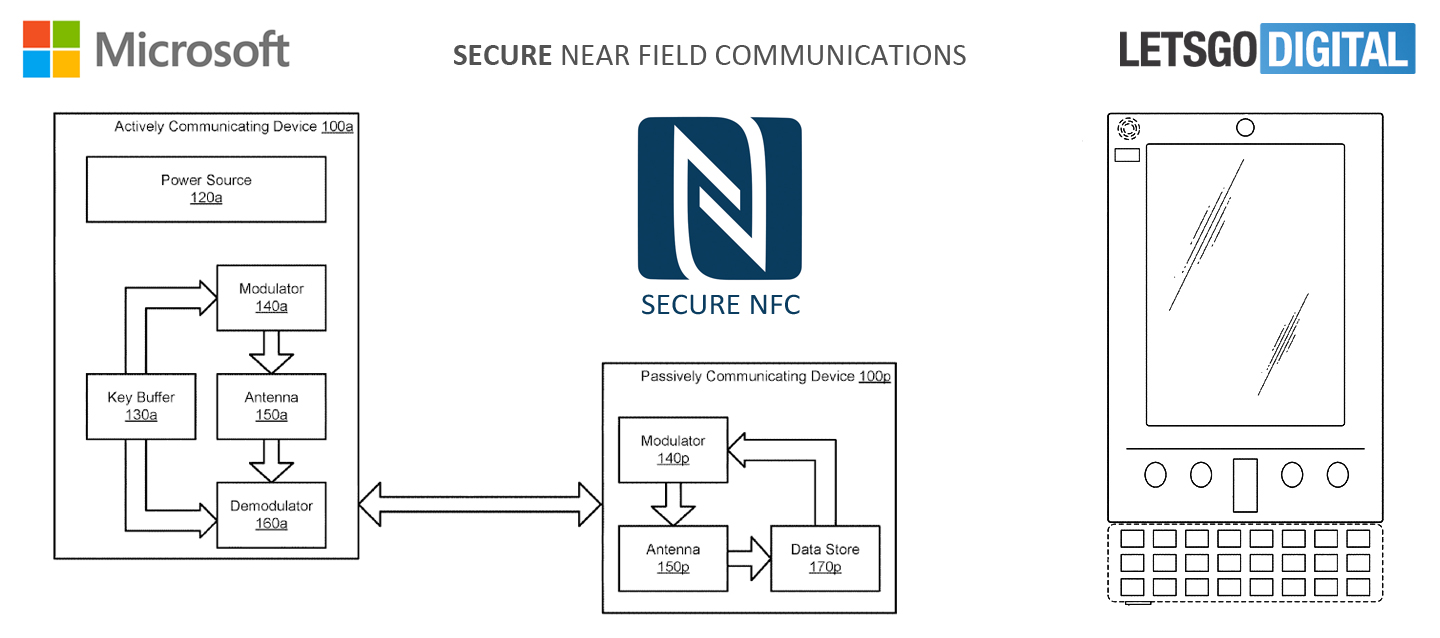
Secure Near Field Communications by encoding a hidden key
The security of Near Field Communications against eavesdroppers is improved by encoding a hidden key, private to an initiating device, onto the carrier wave when a target device communicates its data via the carrier. The initiating device, in possession of the hidden key, is enabled to undo the scrambling effects of the hidden key to thereby privately interpret the data encoded onto the carrier wave by the target device. In various aspects, the hidden key is a one-time-use key that is randomly generated, used, and then discarded, preventing malicious parties from gaining the hidden key to later interpret intercepted data signals.
The passively communicating device encodes its data onto the carrier oblivious to the modulation, and the actively communicating device maintains a cache of the modulations so that their effect on the communications from the passively communicating device can be removed by the actively communicating device.
The actively communicating device receives data from the passively communicating device that is interpretable by the actively communicating device, but eavesdropping devices receive a signal that is scrambled and uninterpretable. The actively communicating device privately maintains the hidden key used to modulate the carrier, and may discard the key as the signal is interpreted to forgo the possibility that an eavesdropped may recover the hidden key and thereby interpret intercepted messages.
The patent from Microsoft can be seen here.
Advertentie